CUI: The Complete Guide to Controlled Unclassified Information
Learn what CUI is, how to identify it, and how to protect it.

[Free Download]
Questions and Answers for the DoD Mandatory CUI Training
What Is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information (CUI) is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.
CUI can include a wide range of information, such as personal information, proprietary information, or information that is considered critical to national security.
It is important to properly handle CUI to ensure that it is not inadvertently disclosed to unauthorized individuals.
What are CUI assets?
Controlled Unclassified Information (CUI) assets are assets that process, store, or identify CUI.
Controlled Unclassified Information assets are essential to the success of a DIB organization in its support of the DoD, so identifying these assets should be at the top of the list when it comes to not only compliance but healthy cybersecurity practice as a whole. Organizations should clearly define the workstations, file servers, cloud collaboration services, and/or managed service providers.
Read more: How to Identify CUI Assets
Types of CUI: CUI Basic vs CUI Specified
Within the NARA CUI Registry, there are 125 total CUI categories listed that are divided into 20 index groupings. An investigation into the CUI category for the data will reveal its type: CUI-Basic or CUI Specified.
What is CUI Basic?
CUI Basic is CUI that only requires applying NIST 800-171 to protect such information. If you see the CUI Basic marking, unless otherwise educated with other controls, you're going to apply NIST 800-171 in that environment and around that data.
CUI Basic contains the baseline handling and dissemination controls as identified in the Final Rule issued by NARA (the National Archives and Records Administration) on November 14, 2016.
The Federal Information Systems Modernization Act (FISMA) requires that CUI Basic be protected at the FISMA Moderate level and must be marked as CUI.
What is CUI Specified?
CUI Specified is a subset of CUI where the authorizing law, policy, or regulation puts more restrictive controls on the handling and control of the content.
CUI Specified is CUI that has a law, regulation, or government-wide policy saying you have to do things above and beyond NIST 800-171 to protect the data.
For example, you must comply with DFARS 7012 which says you have to (among other things):
- Do cyber incident reporting with covered defense information
- Do flow-downs for potential forensic imaging
- Have an appropriately built external cloud provider if you are using such technology
The underlying authority maintains the handling controls on CUI Specified content and ONLY a designating agency may apply the limited dissemination controls to CUI content. This cannot be done by an agency that was not the original designating authority.
More importantly, agencies cannot increase CUI Basic’s impact level above moderate external to their agency without an agreement with the external agency or contractor organization operating an information system on their behalf.
Identifying and Categorizing CUI
When trying to determine if your organization has CUI, try asking yourself these questions:

- C – Is the data originally Created by the government and provided to you in association with the contract?
- U - Is the data going to be Used to deliver your contractual responsibilities to the government?
- I - Can the data type be Identified within the sub-categories listed on the NARA CUI registry?
These three criteria should help you navigate figuring out whether the data you're handling is CUI.
Here's something else that might help you identify whether or not you're handling CUI. This a copy of what the DoD typically workshops in their public documentation. We changed the verbiage a little bit for simplicity's sake.
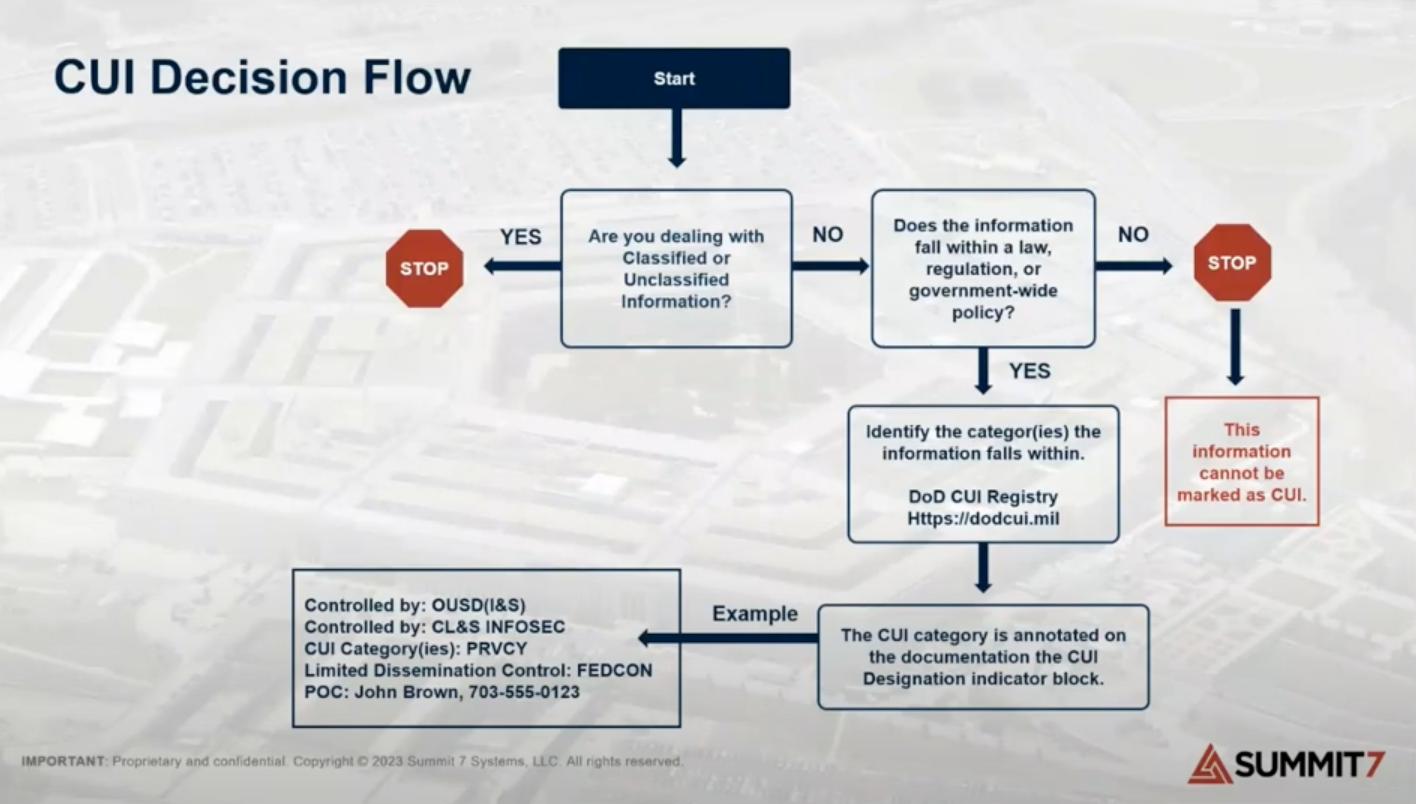
The first question is, are you dealing with classified or truly unclassified information?
Next up, does the information fall within a law, regulation or government-wide policy? If not, it's not CUI.
All of the proprietary data you have – if you're not delivering on a contract and it doesn’t call it out as something unique to the government – it's probably not CUI.
If it does have a law, regulation or government-wide policy, you'll need to look up those categories in the National Archives or the DoD CUI Registry. We'll do that in the next step.
Before we do, though, let's take a quick look at a Microsoft tool you can use to help find CUI.
Identifying CUI with Microsoft 365
Microsoft Purview helps defense contractors identify Controlled Unclassified Information (CUI) in their IT systems to comply with CMMC 2.0 requirements.
The following blog discusses how Organizations Seeking Certification (OSC) can effectively identify CUI in their current IT environment using the Microsoft 365 platform:
Identifying CUI with Microsoft 365 For CMMC
How to Identify CUI Outside of Microsoft 365
As you work through the process of identifying CUI, one question that might come up is around how to find CUI data outside of Microsoft 365.
Locating data containing CUI outside of your Microsoft 365 environment is a bit of a process. You'll need to map all your internal processes and data flows to identify potential areas where CUI might be residing outside of Microsoft 365.
We have a CMMC Level 2 solution with a specialized CUI scoping project dedicated to addressing precisely this challenge. Our team can provide the necessary expertise to guide you through the process of identifying and relocating the non-M365 data containing CUI securely.
If you're interested in learning more about our CMMC Level 2 solution and CUI scoping project, reach out to us here.
Walkthrough of CUI Categorization
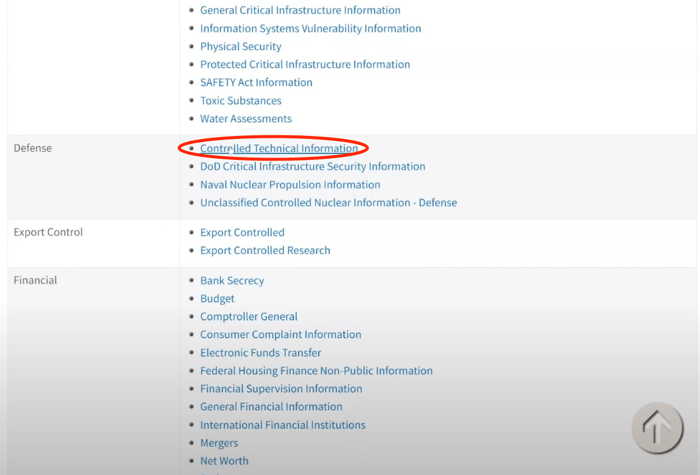
For this example, we're going to use the National Archives CUI website. Visit the website, then click on Category list.

You’ll see a column called Organizational Index Groupings with the CUI categories underneath.
One of the examples we like to talk about when it comes to CUI is Controlled Technical Information, which is found next to the Defense section.
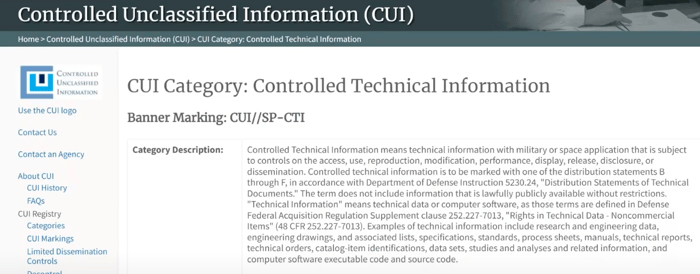
If you click Controlled Technical Information, you’ll see a category description. This one has a long category description, but it’s basically telling you what CTI is, where the reference documentation is located, that DFARS 7013 has the definition and other helpful information.
As you read through it, you might start to think that everything is CUI. But if you look all the way down at the very bottom of the Controlled Technical Information page, you’ll see a table with a heading titled Safeguarding and/or Dissemination Authority.
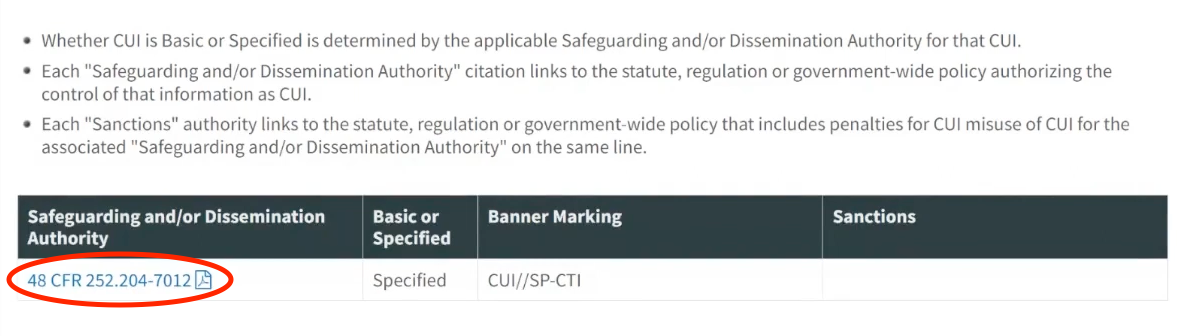
This is going to tell you which reference document to look at to determine if this applies to you. It’s also going to tell you if it's Basic or Specified CUI as well as the banner marking that you're going to need if/when you mark it.
But if you click the link under the Safeguarding and/or Dissemination Authority heading, a document will be opened that will tell you things like which types of systems that you need, how you need to configure them, which type of a cloud environment you need to use – and it’s all wrapped up in this document.
For the sake of this example, do a search in the document for “Controlled Technical Information” and you’ll see the definition of what CTI is.
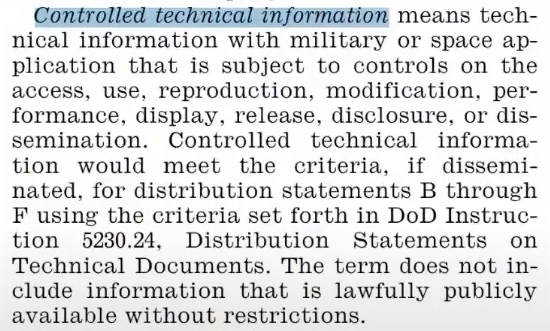
It even goes into things like distribution statements that you might see coming from the DOD.
But this poses another great question. You might think, “Okay, I get the word “controlled,” is there a better definition of what "technical information” is?
If you scroll over within that same clause, it actually tells you that “technical information” means technical data or computer software as those terms are defined in the referenced DFARS clause.
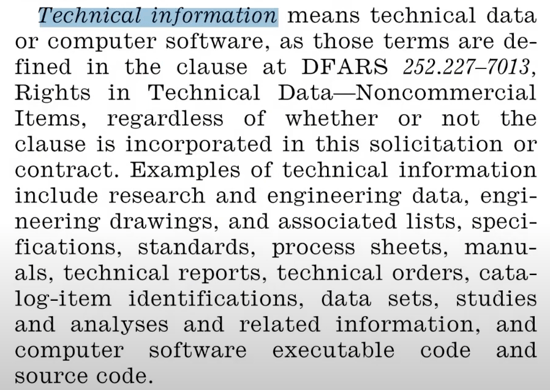
And if you look at what that clause is called, Rights in Technical Data for Non-Commercial Items, you can tell something just from that: it means this definition does not apply to consumer off the shelf items. If you can go to Walmart and pick up, then this clause doesn’t apply.
But to dig a little deeper, you’ll next want to do a Google search for the clause that’s referenced in the document. In this case, it’s “DFARS 252.227–7013”. If you do a Google search for it, you’ll find a page on Acquisition.gov with the document on it.
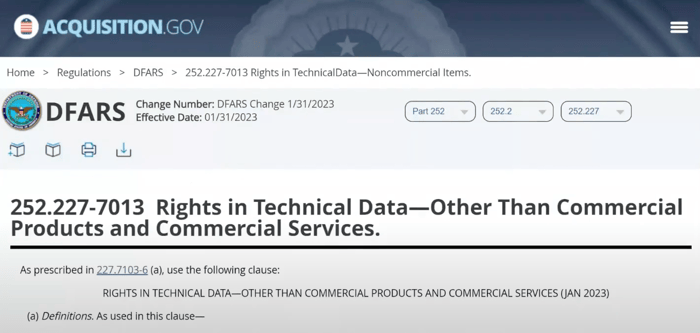
As you're going through that page, you'll see that it covers definitions of computer database, computer program, and computer software.
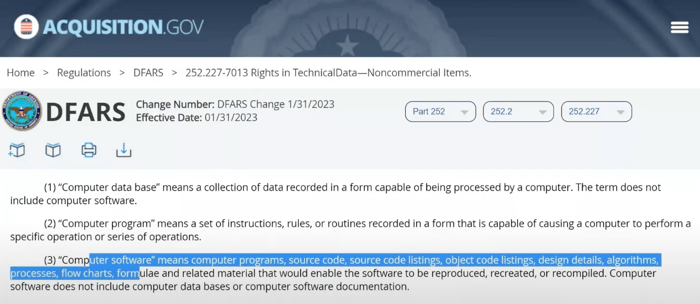
This is what helps you refine and understand if the data you're handling is actually going to be CUI, or in this case Controlled Technical Information.
Read more: Identifying CUI with Microsoft 365 For CMMC
Common Mistakes with Identifying CUI
It's important to remember that not everything is CUI.
For example, some companies think their budget should be considered CUI. They might be concerned about different ERP systems and other kind of technologies they have with budget information. And, to be safe, they think it wise to consider it CUI.
But if we look at the CUI categories on the DoD CUI Program site and go to Financial, then go to Budget and look at the actual summarization of the category, what we’ll find it that a budget is only CUI Specified when it's a budget for federal agencies. As long as you're not a federal agency, it's not CUI.
Another thing to consider is whether this CUI has a government-wide policy, law, or regulation in place that applies to contractors. Going back to our budget example, if you're not a federal agency reporting your budget to the Office of Management and Budget, then there's no reason to consider it CUI.
Marking CUI
This video from the US National Archive explains how organizations can properly mark CUI data. Summit 7 does not own the rights to this video.
History of CUI
The CUI Program was established as a result of Executive Order 13556 and is intended to standardize the way the government and those doing business with the DoD handle and protect unclassified information.
Prior to the current CUI program, every agency used a different set of markings (FOUO, LES, SBU, UCTI, etc.), information classifications, and rules for how to manage and control the information.
Many organizations in the Aerospace and Defense industry may have become accustomed to markings being applied to data such as:
- For Official Use Only (FOUO)
- Law Enforcement Sensitive (LES)
- Sensitive but Unclassified (SBU)
- Unclassified Controlled Technical Information (UCTI)
- Etc.
All of these are now Controlled Unclassified Information or CUI.
This information, although unclassified, is still crucial to national defense and it warrants special protection to prevent unauthorized access or disclosure.
CMMC 2.0 compliance and CUI
In 2023, the Department of Defense will finalize the rulemaking process effectively putting the DFARS clause 252.204-7021 into the rotation of contract clauses that can be applied to DoD contracts. As a result, contracting officers and prime contracts will be able to attach this clause to the contract's flowdown Cybersecurity Maturity Model Certification (CMMC) requirements in their supply chains.
You can read more on the requirements for those who handle CUI by clicking the button below.
How do I protect CUI?
- Implement NIST SP 800-171 if you have not already done so.
- Prepare for third-party (C3PAO) or government-led assessments.
- Reach out to a service provider who is able to help you identify CUI and provide next steps for CMMC 2.0 compliance.
Should my business spend money before CMMC 2.0 rules are established?
Protecting CUI with Microsoft 365
Free On-Demand Webinar:
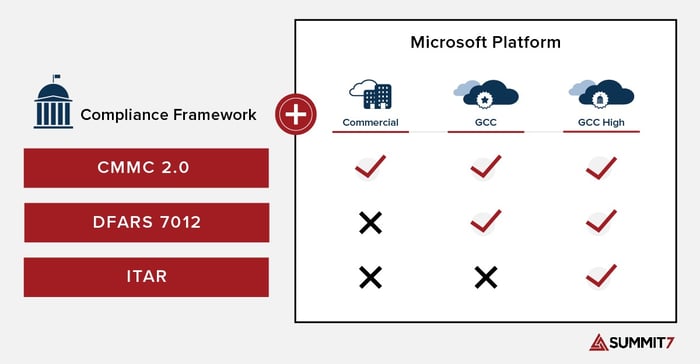
Many contractors in the DoD supply chain have already chosen to handle sensitive data such as CUI and ITAR data in the Microsoft Government Cloud. Microsoft has two versions of M365 that are suited for handling CUI, Microsoft 365 GCC High and Microsoft 365 GCC.
GCC High is not required to meet CMMC 2.0 at any Level. However, Microsoft's official recommendation is for organizations planning or required to meet CMMC 2.0 Level 2 (formerly CMMC 1.0 Level 3) should deploy to Microsoft 365 GCC High.
Resources for getting started with protecting CUI in Microsoft Government:
The graphic below represents the Microsoft Platform as it relates to relevant compliance frameworks such as CMMC, DFARS 7012, ITAR regulations.
DoD Mandatory CUI Training Study Questions
DoD Mandatory Controlled Unclassified Information (CUI) Training is a comprehensive training program implemented by the U.S. Department of Defense (DoD) to educate its personnel on the proper handling, protection, and dissemination of Controlled Unclassified Information.
The training covers topics such as identifying CUI, marking and handling procedures, storage and transmission protocols, incident reporting, and the consequences of mishandling CUI.
By completing this mandatory training, DoD personnel contribute to the overall protection of critical data, maintaining national security, and promoting responsible information management practices.
Below are questions to prepare you for the DoD Mandatory CUI Training:
- Information may be CUI in accordance with a law, regulation, or government-wide policy.
- The correct banner marking for UNCLASSIFIED documents with CUI is CUI.
- The correct banner marking for a co-mingled document containing TOP SECRET, SECRET, and CUI is TOP SECRET.
- I don't have a security clearance, so I don't have to get a pre-publication review. FALSE
- In order to obtain access to CUI, an individual must first have a lawful government purpose.
- Who is responsible for applying CUI markings and dissemination instructions? Authorized holder of the information at the same time of creation
- At the time of creation of CUI material, the authorized holder is responsible for determining: CUI category, CUI markings, and dissemination instructions
- What is the purpose of the ISOO CUI Registry? A government-wide online repository for Federal-level guidance regarding CUI policy and practice
- It is mandatory to include a banner marking at the top of the page to alert the user that CUI is present. True
- What is Controlled Unclassified Information (CUI)? Unclassified information requiring safeguarding and dissemination controls, pursuant to and consistent with applicable laws, regulations, and governmentwide policies
- Administrative, civil, or criminal sanctions may be imposed if there is an Unauthorized Disclosure (UD) of CUI. True
- What level of system and network configuration is required for CUI? Moderate confidentiality
- CUI documents must be reviewed according to which procedures before destruction? Records Management
- What is the goal of destroying CUI? To make it unreadable, indecipherable, and unrecoverable
- What is CUI Specified? The subset of CUI in which the authorizing law, regulation, or government-wide policy contains specific handling controls that it requires or permits agencies to use
- What is CUI Basic? The subset of CUI for which the authorizing law, regulation, or government-wide policy does not set out specific handling or dissemination controls
- What marking (banner and footer) acronym (at a minimum) is required on a DoD document containing controlled unclassified information? CUI
- Who can decontrol CUI? OCA, if in a Security Classification Guide, or the designated office for decontrolling
- What DoD Instruction implements the DoD CUI program? DoDI 5200.48, Controlled Unclassified Information
- Who is responsible for protecting CUI? DoD military, civilians, and contractors
Frequently Asked Questions About Controlled Unclassified Information (CUI)
Does a picture of a part or part number related to an ITAR drawing qualify as CUI?
The most important question is: is it marked?
The next most important question is: have you asked the information owner?
It really depends on what's included in a drawing as to whether it should be considered ITAR data. But the contracting officer should understand what that is.
If it’s an individual part, then there’s a chance it could have been de-controlled or segmented upon sending to you. But again, don’t assume. Ask the information owner.
You do not want to be liable for disclosure of information that is sensitive to the Department of Defense. The penalties can be severe – to include jail time – for these types of violations.
Is a part number taken from an ITAR drawing and then used in the company’s ERP system to support considered CUI?
Part numbers traditionally aren’t CUI by themselves. You should contact a lawyer to have a better understanding of that. But if it’s an independent part number with no correlation to what it is, then you’re probably safe.
If a CMMC required client has no desire to keep any CUI in the cloud or email is GCC or GCC High necessary?
If you’re not keeping anything in the cloud, you probably don’t need a cloud provider. If you anticipate getting no CUI in email, then you don’t need GGC High for collaboration. If email is not in scope, do a content search to see if any CUI is present.
What is a good approach for commercial companies that have only a small part of their business that handles ITAR data?
If you are under a hundred people, it is typically recommended to not have an enclave because the management burden becomes very high. We usually recommend doing a “lift-and-shift" (all-in) if the company is smaller and you want to collaborate consistently in the same way.
However, if you have less than 5-10% of your employee base handling ITAR data and you are a larger company, usually an enclave is a better approach.
How does a company manage CMMC when they utilize 3D CAD systems such as SolidWorks or Fusion?
You can manage and secure those physical devices using something called Intune or leverage an optimized version of Azure Virtual Desktop to do things like SolidWorks, Autodesk, or any kind of AutoCAD program.
Does Summit 7 ever recommend Microsoft 365 Commercial plus PreVeil or bolt-on email drive for CUI?
We don't recommend bolt-on email tools and email drives first and foremost because of the user hurdles involved. We want a seamless collaboration environment and to avoid having the user jump through a lot of hoops.
The last thing you want to worry about is whether the email tools you have in place for capturing and sending sensitive data are being used appropriately by your staff, and whether that data is circulating outside of those secure environments (i.e., M365 Commercial).
There’s also a very good chance that email is not the only place you’re storing sensitive data. For those reasons, we recommend a secure Microsoft Government cloud that provides a simple, no-user-impacting scenario for securing that sensitive data.
How can I know for sure if we need to meet CMMC level 1 or CMMC level 2?
If you have a DFARS 7012 clause in your contract, it tells you how to protect CUI data. In order to protect CUI, you’ll need to know if you actually have CUI in your environment.
To do that, look at the contract you signed, look at the deliverables, and have a conversation with your contracting officer on if that's CUI, and if so, what type of CUI it is.
Here’s a more comprehensive look at the differences between CMMC levels 1, 2, and 3.
Do you no longer need your on-premises server if you move towards Microsoft 365 GCC or GCC High?
It depends on what the server is doing.
To eliminate on-prem servers when you migrate to the cloud, you can either potentially offset some of the things the on-prem server was used for – such as device joins – or if that server is doing a specific line of business application that you have, while you can't put it in GCC High, you can still put it in Azure Government. So, you can still virtualize an on-prem server and put it in a compliant data center in order to check the compliance box.
Does an MSP supporting a GCC High client require CMMC certification?
Right now, there is not full clarity around what the CMMC requirement will be for MSPs, but at a minimum MSPs will need to understand that, if they are managing export control data, only US persons can have administrative access and they will need to have a shared responsibility matrix mapped to NIST 800-171A on what controls the MSP is meeting on the client’s behalf.
What causes Microsoft Commercial to fail to meet the requirements for NIST 800-171?
NIST 800-171 is not a compliance standard, it is a control set. The additional requirements covered under DFARS 7012 cannot be met by Microsoft Commercial because of the reporting requirements under paragraphs c-g (incident response requirements).
Do we still need the Microsoft Government cloud if we are encrypting sensitive emails and not using SharePoint to store data?
Yes, because of the US person's requirements and the incident response and flow down requirements found in DFARS 7012.
DFARS 7012 requires forensic imaging and incident response that cannot be met by simply encrypting emails.
Sure, there are things like carve-outs for ITAR/EAR data that allow for data to be encrypted to FIPS 140-2, but the incident response and forensic imaging piece is still at play if your contracts are subject to DFARS 7012. You're not immune to that even with encrypted data.
Migrating from Microsoft Commercial to Microsoft GCC High, are there any steps that are different from migrating to Microsoft GCC?
The difference between migrating to GCC High and migrating to GCC are subtle. The primary differences lie in GCC High’s nuances with things like B2B collaboration, setting up external users, teams audio conferencing, and phone system routing.
Outside of that, the migration processes for both GCC High and GCC are pretty much identical. However, if an organization moves from Commercial to GCC then discovers that it needs to be in GCC High at a later time, there is an additional migration involved. This is why it is so important to consider the long-term impacts of a Migration to the right cloud.
Is there a way to configure Google for compliance with CMMC Level 2?
You can configure Google for CMMC compliance up to a point. However, when you get into handing export control data, there are different agents and integrations that you would have to do carve-outs for. So, you can, it's just difficult in the long run. And if users try to circumvent it, then you might have other security issues on your hand.