The Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012: Safeguarding Covered Defense Information and Cyber Incident Reporting is the oldest of four clauses in the recently expanded DFARS 70 series (7012, 7019, 7020, and 7021). DFARS 7012 applies to ALL Department of Defense (DoD) acquisitions, except for Commercial Off the Shelf (COTS) items, and requires contractors to implement technical and procedural controls as specified by the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 to protect sensitive information and to rapidly report cyber incidents.
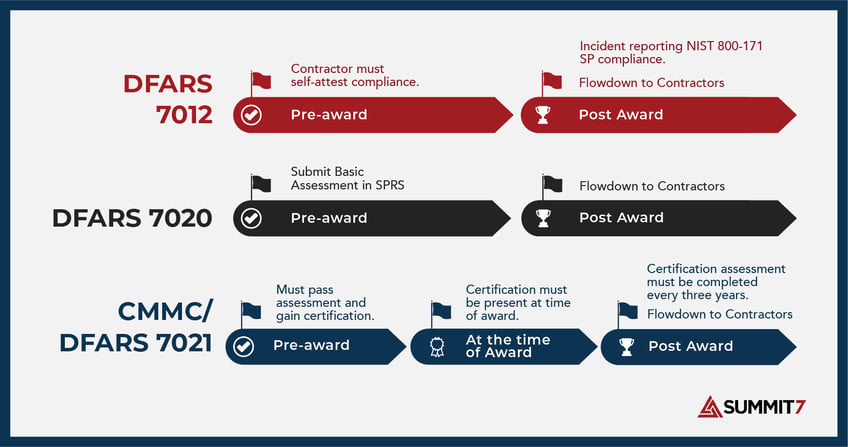
The biggest difference between DFARS 7012 and CMMC is the requirement to "self-attest" versus a formal third-party assessment prior to contract award - in the case of CMMC.
Note: The CMMC proposed rule has officially been published. You can read more here.
If you are a contractor working on behalf of the Department of Defense (DoD) as either a prime or a sub-contractor, then DFARS 7012 is a current insertion within your contract or subcontract agreement. The DFARS 7012 clause went into effect on December 31st, 2017 in a response to data breaches and increasing cybersecurity threats occurring within the Defense Industrial Base (DIB); it is still a requirement today along with the Cybersecurity Maturity Model Certification (CMMC). Read about the overlap with CMMC below.
These regulations only apply to unclassified systems. Systems supporting data classified at the SECRET, TOP SECRET, or TOP SECRET SCI are not covered by these regulations. So, what type of information is covered under DFARS 7012? Specifically, the clause classifies the following information as critical information for protection:
There are 125 categories in the CUI registry as of this writing, which has expanded from roughly 30 in 2017. However, every company will have information that falls into at least four of the most common categories; privacy, procurement and acquisition, proprietary business information, and tax documents. A company may also interact with CUI that falls into the Export Control or Defense categories.
The most common categories that impact almost all companies doing business with the DoD include:
If a defense industrial base organization handles CUI as outlined by NARA and Executive Order 13556, the first step is to identify how it is handled and where it resides in their information systems. CUI is often spread across file shares, email, collaboration systems, proposal management systems, mobile devices, Line of Business (LoB) systems and company laptops.
DFARS 7012, broken down from paragraphs 'a' through 'm', requires aerospace and defense contractors and subcontractors to do the following:
Provide Adequate Security and Safeguard CDI
First, one must define the two different types of systems covered under DFARS 7012. The focus of most DoD contractors will be on Type 2 systems, as that category relates mostly to their internal IT support and collaboration systems.
Type 1 System Definition: DFARS 252.204-7012 (b)(1) defines covered contractor information systems that are part of an IT service or system operated on behalf of the government, the following stipulations apply “(i) Cloud computing services shall be subject to the security requirements specified in the clause 252.239-7010, Cloud Computing Services” DFARS 252.239-7010 (b)(2) “Cloud Computing Services” specifies that the contractor shall implement the appropriate safeguards and controls in accordance with the DISA Cloud Computing Security Requirements Guide (DISA SRG v1r3), unless the DoD CIO has waived the requirement. The DISA SRG v1r3 specifies the NIST 800-53r4 as the control set that must be implemented to be compliant.
Type 2 System Definition: DFARS 252.204-7012 (b)(2) defines covered contractor information systems that are not part of in IT service or system operated on behalf of the Government and are not subject to the security requirements specified in (b)(1); however, the following security requirements apply:
(i) The covered contractor systems shall be subject to NIST 800-171
(ii) The contractor shall implement NIST 800-171 and if the contractor intends to use an external cloud service provider then the cloud service provider must meet the requirements established by FedRAMP Moderate and comply with paragraph (c) through (g)
A contractor must operate Type 1 System in accordance with the DISA SRG v1r3 and the NIST 800-53r4 control set. Type 2 systems require 110 controls within NIST 800-171. However, if the contractor uses an external Cloud Solution Provider (CSP), that CSP environment must be at minimum FedRAMP Moderate compliant. Bottom line, the DFARS requirements levy a much higher set of requirements on Type 1 systems vs Type 2 systems. This is good news for contractors, but it is still a significant undertaking for almost all organizations.
A note on external Cloud Service Providers (CSPs) and FedRAMP Moderate "Equivelancy": Since 2016 DFARS clause 252.204-7012 has said that if a contractor puts CUI in the cloud then the contractor needs to require and ensure that the cloud service provider meets security requirements "equivalent" to the FedRAMP Moderate baseline.
On 12/21/23, the DoD released a memo clarifying the stringent requirements of FedRAMP moderate “equivalency”– and it’s effective immediately. DoD Contractors are now on the hook for their Cloud Service Provider’s (CSP) FedRAMP compliance. According to the memo: the DoD requires a lot of contractors with defense data being stored, processed, or transmitted with a FedRAMP Equivalent CSP.
A FedRAMP Moderate Authorized CSP will require considerably less effort by the contractor. You can check if your CSP is Authorized on the FedRAMP marketplace. If you do have an FedRAMP moderate "equivalent” CSP, you might consider switching to a FedRAMP-Tailored Solution. We recommend either Microsoft GCC or GCC High.
Support for FedRAMP in the Microsoft Government Cloud
A recent blog from Microsoft explains the unique position of GCC High being equivalent and in process of re-authorization:
"The DoD memorandum for ‘FedRAMP Moderate Equivalency for Cloud Service Provider’s Cloud Service Offerings’ establishes the definition of ‘Equivalency’. Please note the second paragraph of the memo:
This memorandum does not apply to Cloud Service Offerings (CSOs) that are FedRAMP Moderate Authorized under the existing FedRAMP process.
With this established, any cloud service that falls under the Azure Government P-ATO is fully covered and advertised in the FedRAMP Marketplace as ‘Authorized’.
For the Office 365 GCC High cloud services, we can demonstrate compliance with FedRAMP Moderate ‘Equivalency’ with our BoE in the manner the memo describes. Fundamentally, the memo requires a CSP to do all the activities leading to a FedRAMP Agency ATO or P-ATO, minus the FedRAMP PMO’s review. Microsoft has done the FedRAMP Agency ATO process numerous times and is in the process of finishing the PMO’s review. Microsoft’s BOE will suffice to meet any FedRAMP Moderate equivalency review by assessors and members of the Defense Industrial Base."
Report Cyber Incidents
In response to an incident or cyber event, DFARS requires your organization to notify DoD through formal reporting mechanisms and DoD will need access to your environment - including cloud tenants and other cloud systems handling CUI.
Note: This section is where issues may arise. In the event of an incident, a report must be created for the DoD and it must include any malicious software recovered and isolated during the incident, as well as images and logs of all affected information systems for at least 90 days from the submission of the cyber incident report. This requirement means that both the contractor and any cloud computing service used by it must maintain a running 90-day log and provide system images for any systems which store, process, or transfer CDI or CUI, which is why many organizations choose Microsoft 365 GCC High or GCC.
As mentioned above, if a reported cyber incident occurs, the subcontractor or contractor must also submit the malicious software here: https://dibnet.dod.mil/portal/intranet/
Contract Flowdown
The third primary component of the DFARS 7012 clause requires all prime contractors and subcontractors to include the DFARS 7012 clause, in its entirety, in all related subcontracts without alteration. This component is straightforward and ensures that all potential providers or organizations that could have access to CUI/CDI data are covered by the DFARS 7012 clause. Microsoft meets these flowdown requirements with its Government Cloud offerings, which you can see here.
Now that you have a basic understanding of what is covered in the DFARS 7012 clause, you may want to know what the cost of these new requirements will be to your organization. For almost all organizations, this is going to be a six-figure problem. The size and complexity of the policy, technical and support environment needed to get and maintain compliance is very significant, and it doesn’t vary much for companies from 1-500 users. Larger organizations in the thousands and tens of thousands of employees could easily reach seven figures or higher to ensure compliance. Thankfully many of these costs are redundant to CMMC.
DFARS 7012 and CMMC overlap in several fundamental ways. At the outset, CMMC requirements are established in DFARS via DFARS 7021; every DIB supplier will have both requirements moving forward - especially after 2025. Also, the same flowdown requirements are present in CMMC, and all subcontractors must follow similar requirements as the prime. Lastly, the most common thing shared among both regulations, is the shared implementation of NIST 800-171. CMMC Level 2 includes all of NIST 800-171's 110 controls.
If you still have questions about DFARS 7012, or you would like to discuss something else, please do not hesitate to reach out to us.
Here are some ways you can stay connected to the Summit 7 team and hear the latest on all things security and compliance: