4 Advantages to Become CMMC Compliant Before the CMMC Rule
The DIB simply cannot wait until the CMMC Rule is imposed to be compliant. Here are four advantages to comply prior to a CMMC Rule.
Although many know that CMMC will be required for Defense Industrial Base (DIB) contractors, many still remain hesitant to start preparing and implementing controls under the NIST 800-171 framework. However, in the case of CMMC, the process to implement controls takes far too long to wait til the last minute.
So, why is the DIB waiting on CMMC? A CMMC rule is imminent that will assess DoD contractors on the compliance standards outlined in NIST SP 800-171 since 2017. Above all, this is not merely about complying with regulations, but sets a precedent for safeguarding Controlled Unclassified Information (CUI) and the future of your business. This post will highlight four distinct advantages of becoming compliant before the CMMC rule.
4 Advantages to Becoming CMMC Compliant Before the CMMC Rule
- Early adopters will benefit from a competitive advantage
- Implementation providers' lead times will be pushed further into 2023 and 2024
- CMMC will be the key to safeguarding your business and future-proofing organizational legacy
- It is your contractual obligation to protect CUI
Bonus Section: Will Bad Security in the DIB Accelerate Rulemaking?
1. Early Adopters Will Benefit
By making the choice to become CMMC compliant now, organizations gain a massive advantage over their competitors. Small-to-medium sized businesses (SMBs) that have taken the steps to obtain their certification early will be highly sought after and more marketable to prime contractors looking for acquisition targets.
Mergers and Acquisitions in the DIB can offer tremendous drivers for growth—expand capabilities, add greater value to its customers, and provide a competitive advantage in the market.
Early adopters recognize that the same flowdown requirements are present in CMMC as DFARS, and all subcontractors must follow similar requirements as the prime. DFARS 7012 and CMMC overlap in several fundamental ways. On the outset, CMMC requirements are established in DFARS via DFARS 7021; every DIB supplier handling or processing CUI will have both requirements moving forward.
Lastly, the most common thing shared amongst both regulations, is the shared implementation of NIST 800-171. CMMC 2.0 Level 2 includes all of NIST 800-171's 110 controls.
Currently under DFARS 7020, DoD suppliers and contractors supporting contracts would need to demonstrate their level of NIST compliance by posting their self-assessment score to SPRS as a requirement for obtaining new contracts or maintaining existing ones.
There is also the chance that NIST 800-171 rev3 is announced in the late Spring of 2023. Those who have yet to implement NIST 800-171 will likely assume more controls from the updated version. CMMC early adopters that are ready for assessments now are unlikely to be affected by the updates from NIST under an interim final rule scenario.
2. Lead Times - Lifeboats Could be Limited
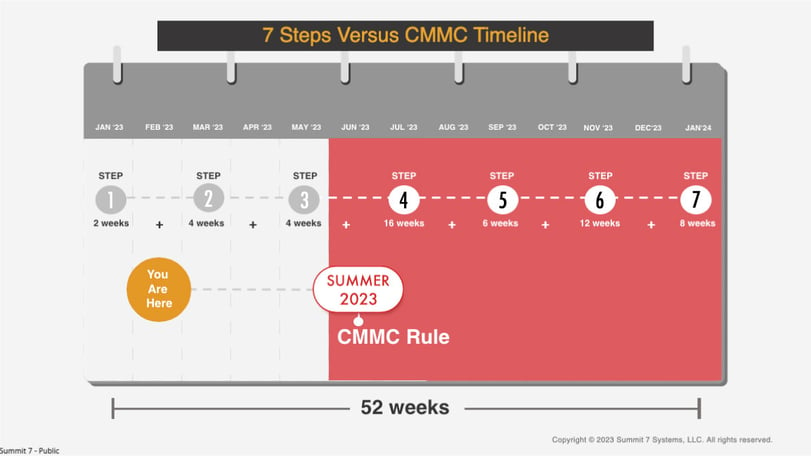
Many, if not most of the DIB and higher education institutions will be required to meet CMMC 2.0 Level 2. The 7 Steps of CMMC outlines the steps it takes to achieve CMMC compliance. On average you can expect to take 12 - 18 months to achieve CMMC compliance.
When you compare that to the possibility of a CMMC rule in May 2023, your organization is already way behind. The longer your organization waits, the further your timeline gets pushed to achieving compliance.
3. Keeping Your Enterprise in Business
Sounds simple, but if your enterprise relies on government contracts to conduct business, you simply cannot neglect compliance. The DoD has made it very clear: no CMMC, no DoD contracts. Look beyond your government contracts for a moment. Taking proper cybersecurity measures safeguards your business from costly cyber threats that can drag on for months after an incident and in some cases close businesses that cannot recover. The costs associated with cyber threats can vary greatly but might include:
- Lost data: Victims may be forced to spend money to restore or recover data that was stolen or corrupted in the attack.
- Lost productivity: If an attack shuts down your system, it can take time for it to be restored. This means lost productivity while the system is offline.
- Legal fees: In some cases, victims may face legal action, including lawsuits or fines, related to the attack especially in the case if ITAR or export control data.
- Damage to reputation: A cyber attack can be damaging to the reputation of your business, which could have a long-term impact on customer loyalty and sales.
- Loss of customers: In this case, loss of contracts
Taking the proper steps to ensure your business stays afloat at the end of the day is vital to your employees and the bottom line of your business.
4. Your Contractual Obligation: Don't Give Up the Data
This is why CMMC exists, right? If your organization handles or transmits CUI you have a contractual responsibility to protect that data under DFARS 7012. You could also conclude that compliance is not solely about protecting the government's data, it is also critical to your organization's overall cybersecurity posture, protecting your systems and data.
All organizations are at risk, especially small to medium-sized contractors based on current industry research. An espionage program, targeting a subcontractor of Lockheed Martin led to the breach of F-35 data. That's why we see China's J-31 and the stark resemblance to the F-35 design.
These types of breaches are not waiting on a CMMC rule, and frankly, the DIB should not either.

China's hacking program is larger than every other major nation combined. If you think a spy balloon is a giant vacuum sucking up all communications in its path, realize the US is losing the war on data every day. Just because it is not floating overhead, does not diminish the risk it poses to the nation. Our innovation, trade secrets, and intellectual property are being targeted on a level that has never before been seen in history.

Protect America’s data. Protect CUI and ITAR. Protect the Sweat.
What Should You Do?
Compliance is of utmost importance from the beginning, not just after signing a contract. If you are uncertain of the current process and preparations, it is beneficial to seek expert advice.
Join Summit 7 and other industry leaders for the latest Cloud Security and Compliance Series (CS2). Cs2 provides ongoing, relevant information for members of the Defense Industrial Base seeking to fulfill government compliance requirements. This series offers essential insight into:
- CMMC 2.0
- NIST 800-171
- DFARS 70 Series (7012, 7019, 7020)
- ITAR regulations
- Protecting CUI and FCI
CS2 is particularly beneficial for aerospace and defense contractors, as well as higher education institutions, who want to become more proactive in security protection, cybersecurity culture-building, and leveraging cloud investments. CS2 is a hybrid event, offering in-person or virtual attendance. Learn more here.
Frequently Asked Questions Around CMMC:
- We are a subcontractor on a DoD contract. Does my organization need to be CMMC compliant?
- If you have existing DFARS 7012 requirements and you handle CUI, it is likely that you'll need to be CMMC Level 2 compliant
- If you have existing DFARS 7012 requirements and you handle CUI, it is likely that you'll need to be CMMC Level 2 compliant
- Should we just wait and see what the DoD does?
- No - It could take organizations anywhere from 12-18 months from start to finish
- No - It could take organizations anywhere from 12-18 months from start to finish
Bonus: Will Bad Security in the DIB Accelerate Rulemaking?
Rumors about delays in CMMC rulemaking never seem to address the elephant in the room: the basis for previous DFARS cybersecurity interim final rules is just as valid today as it was in 2016 and 2020. Is there a better way of analyzing the current state of cybersecurity in the DIB that helps predict how CMMC rulemaking is “likely” to play out?